BLACK FRIDAY
85% Discount for all November
85% Discount for all November

Computer Science
Cyber Security
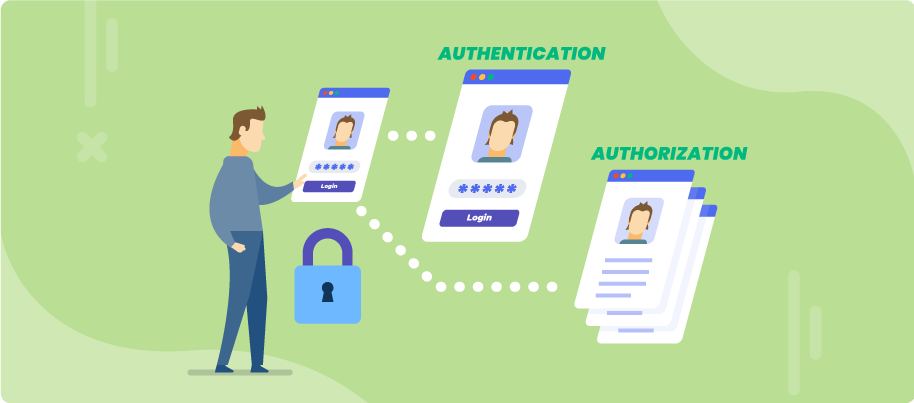
A user authentication policy is a process in which you verify that someone who is attempting to access services and applications is who they claim to be. This can be accomplished through a variety of authentication methods, such as entering a password into your laptop or phone or a PIN number into the ATM.
What is the purpose of authentication?
Authentication is used to verify that you are who you say you are. After a user’s identity is confirmed, for instance with a username and password, that identity may be used in an authorization policy to determine the appropriate access privileges. Organizations today must ensure that the right users are given access to the right resources, whether it is physical or--increasingly--digital.

What are the different authentication protocols?
Network authentication protocols are used to help securely transfer identity credentials for authentication between the subject (user or device) and the authentication server. There are several different authentication protocols for network access control, including:
-> Kerberos
-> Extensible Authentication Protocol (EAP)
-> IEEE 802.1X
-> Remote Authentication Dial-In User Service (RADIUS)
-> Terminal Access Controller Access-Control System (TACACS)
How do I benefit from a user authentication policy?
A user authentication policy may be used to help ensure that only the intended audience is accessing certain assets in your organization. User authentication policies strive to ensure that the person requesting sensitive information and data is the right person to access that information.
Authorization is the function of specifying access rights/privileges to resources, which is related to general information security and computer security and to access control in particular. More formally, "to authorize" is to define an access policy.
The HTTP Authorization request header can be used to provide credentials that authenticate a user agent with a server, allowing access to a protected resource.
The Authorization header is usually, but not always, sent after the user agent first attempts to request a protected resource without credentials. The server responds with a 401 Unauthorized message that includes at least one WWW-Authenticate header. This header indicates what authentication schemes can be used to access the resource (and any additional information needed by the client to use them). The user-agent should select the most secure authentication scheme that it supports from those offered, prompt the user for their credentials, and then re-request the resource (including the encoded credentials in the Authorization header).
That was all about Authentication & Authorization. Drop a like and share it if you found it informative.
Thank you. Have a nice day, let's meet in the next blog!
Wednesday, Dec 8, 2021